Introduction to the XZ Utils backdoor
The XZ Utils backdoor is a sophisticated and malicious software vulnerability that has been lurking in the shadows of the digital world. In this article, I will delve into the intricacies of this backdoor, shedding light on its inner workings and the risks it poses to individuals and organizations alike.
How the XZ Utils backdoor works
The XZ Utils backdoor operates by exploiting vulnerabilities in the XZ file compression utility. When an unsuspecting user downloads or opens a file compressed with XZ Utils, the backdoor silently installs itself on the system, granting unauthorized access to malicious actors. This unauthorized access can lead to a wide range of devastating consequences, from data breaches and identity theft to unauthorized surveillance and control of compromised systems.
Impact and consequences of the XZ Utils backdoor
The impact of the XZ Utils backdoor can be devastating. Once installed on a system, it provides malicious actors with unrestricted access to sensitive information, enabling them to carry out various malicious activities. This can include stealing valuable data, compromising confidential communications, and even taking control of critical systems. The consequences of such actions can be far-reaching and potentially catastrophic, leading to financial losses, reputational damage, and compromised national security.
Detection and prevention methods for the XZ Utils backdoor
Detecting and preventing the XZ Utils backdoor requires a multi-layered approach. Firstly, keeping all software and operating systems up to date with the latest security patches is crucial. Regularly scanning systems with reputable antivirus and anti-malware software can also help identify and remove any instances of the backdoor. Additionally, implementing strong network security measures, such as firewalls and intrusion detection systems, can help prevent unauthorized access to systems.
Recent news about the XZ Utils backdoor
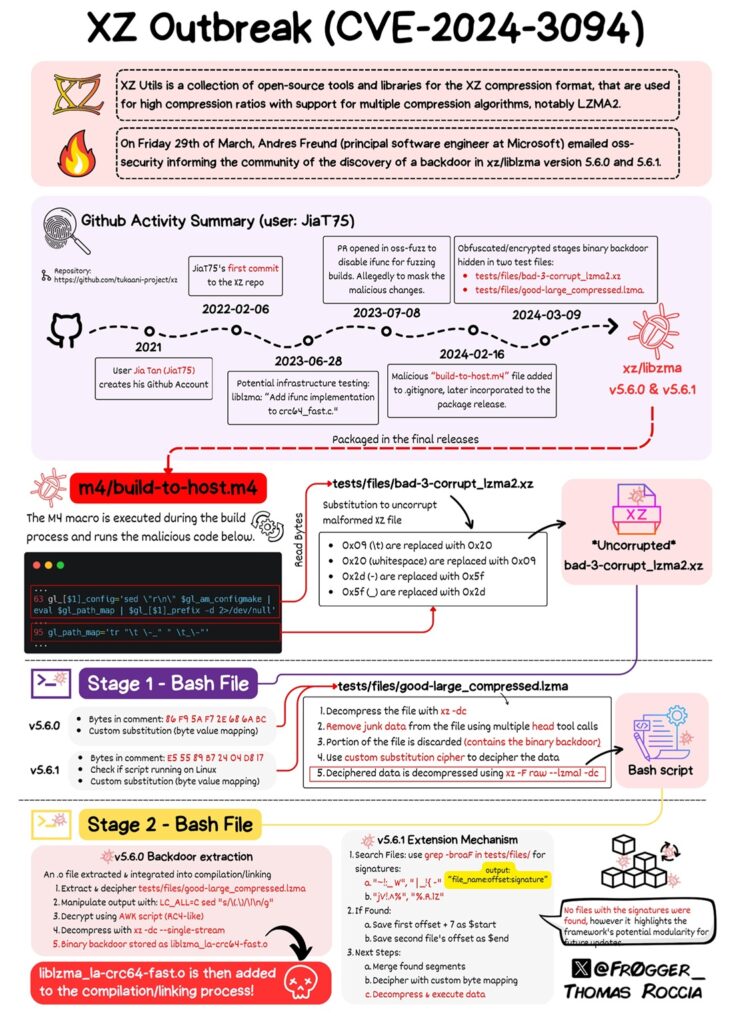
A Microsoft engineer Andres Freund got suspicious of a slightly slower SSH login time (0.299s to 0.807s), and ended up discovering the infamous XZ backdoor.
Reference:
- https://www.openwall.com/lists/oss-security/2024/04/17/7
- https://www.openwall.com/lists/oss-security/
What happened?
Andres Freund, a developer and engineer working on Microsoft’s PostgreSQL offerings, was recently troubleshooting performance problems a Debian system was experiencing with SSH, the most widely used protocol for remotely logging in to devices over the Internet. Specifically, SSH logins were consuming too many CPU cycles and were generating errors with valgrind, a utility for monitoring computer memory.
https://nvd.nist.gov/vuln/detail/CVE-2024-3094
Image Refrence: https://x.com/fr0gger_/status/1774342248437813525
Expert opinions and analysis of the XZ Utils backdoor
Experts in the field of cybersecurity have extensively studied the XZ Utils backdoor, providing valuable insights into its capabilities and potential countermeasures. Many experts believe that the backdoor is continuously evolving, adapting to circumvent detection and exploit new vulnerabilities. Some have also speculated that there may be multiple variants of the backdoor, making it even more difficult to detect and defend against. Ongoing research and collaboration among cybersecurity professionals are essential in staying one step ahead of these sophisticated threats.
Steps for mitigating the risk of the XZ Utils backdoor
Mitigating the risk of the XZ Utils backdoor requires a proactive and comprehensive approach. Organizations and individuals should prioritize cybersecurity awareness and education, ensuring that all users understand the risks and best practices for staying safe online. Regular security audits, penetration testing, and vulnerability assessments can help identify and address any potential weaknesses in systems. Implementing strong access controls, encryption protocols, and network segmentation can also significantly reduce the risk of unauthorized access and data breaches.
The future of the XZ Utils backdoor and potential developments
As technology continues to advance, so too will the capabilities of the XZ Utils backdoor and other similar threats. It is crucial to stay vigilant and adapt security measures accordingly to keep pace with these evolving risks. Continued collaboration between cybersecurity experts, law enforcement agencies, and software developers is vital in developing effective countermeasures and mitigating the impact of these backdoors. The future of cybersecurity depends on our ability to anticipate and respond to emerging threats effectively.
Conclusion: The importance of staying vigilant against backdoor vulnerabilities
The XZ Utils backdoor serves as a stark reminder of the ever-present threats lurking in the digital landscape. Individuals, organizations, and governments must remain vigilant and proactive in their approach to cybersecurity. By staying informed, implementing robust security measures, and fostering a culture of cybersecurity awareness, we can effectively mitigate the risks posed by backdoor vulnerabilities. Together, we can build a safer and more secure digital future.
Safeguard your systems against backdoor vulnerabilities by staying up to date with the latest security patches, using reputable antivirus software, and implementing strong access controls. Remember, prevention is the key to protecting your data and sensitive information. Stay vigilant, stay secure.